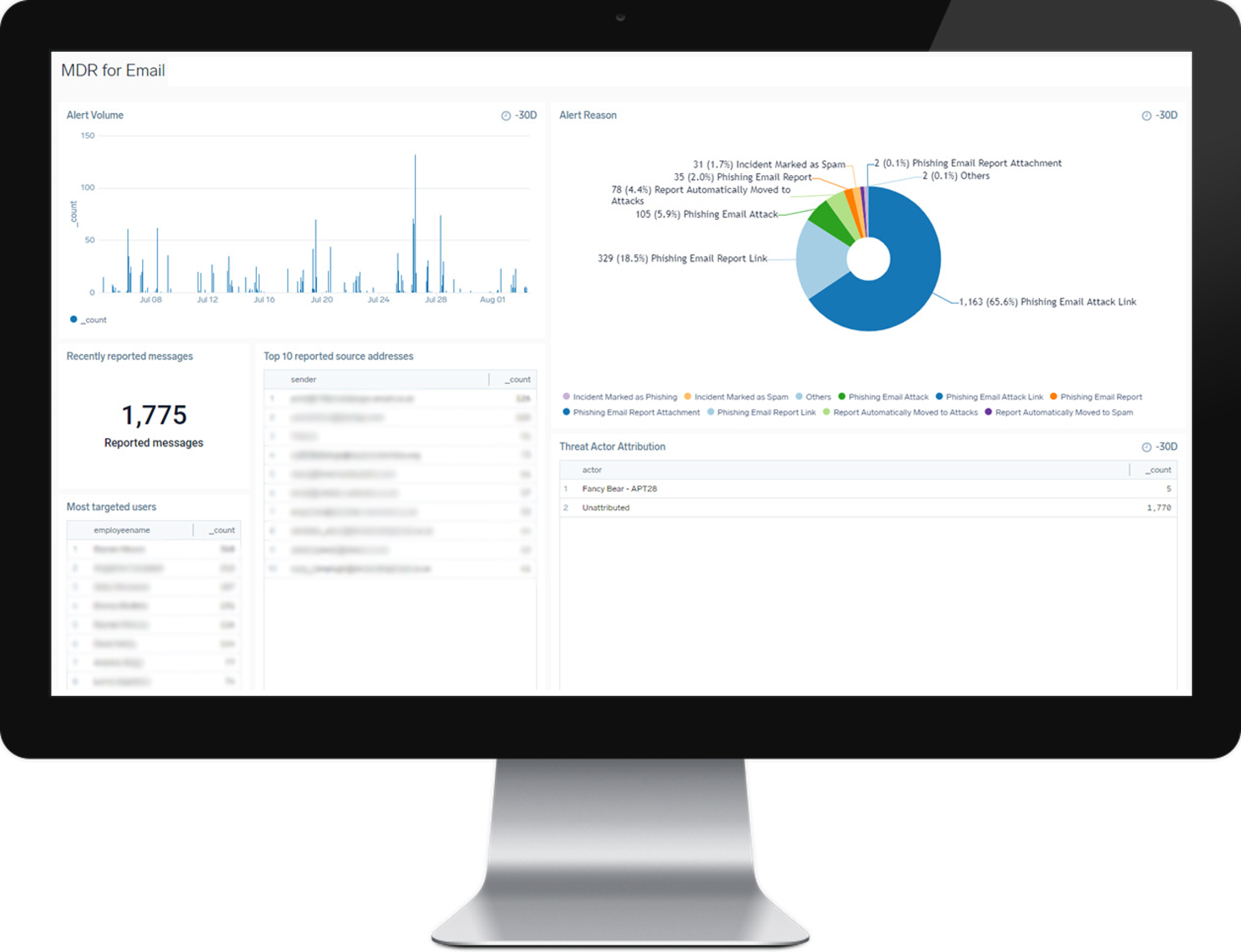
MITRE Aligned MDR
The MITRE ATT&CK Framework is a knowledge base of cyber adversary tactics and techniques based on real-world observations. The Bleam MDR service is developed in-line with this framework to ensure cyber attacks are stopped early in the cyber kill chain.


.jpg?width=1800&height=900&name=Copy%20of%20hero%20banner%201%20(2).jpg)