Biweekly Threat Report
81% Increase in Large-Volume DDoS Attacks

New attacks use Windows security bypass zero-day to drop malware
New phishing attacks use a Windows zero-day vulnerability to drop the Qbot malware without displaying Mark of the Web security warnings. Mark of the Web security warnings are displayed when a file is marked by windows as being downloaded from the web
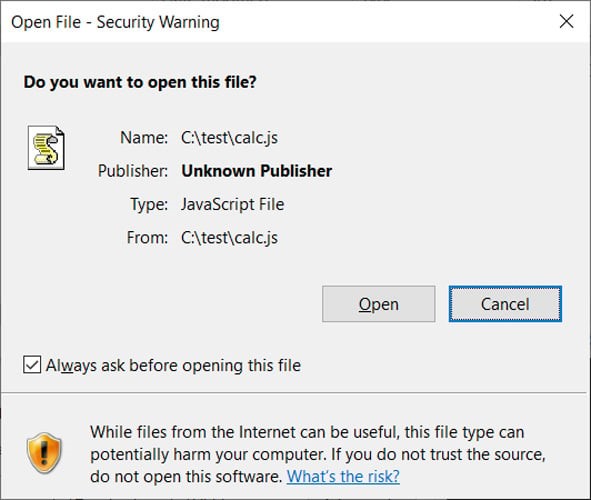
Qbot was using a password-protected ZIP archive containing ISO images. These ISO images contain a windows shortcut and DLLs required to install the malware. Now Qbot has moved to distribute JS files signed with malformed signatures which allows them to abuse the Windows Mark of the Web zero-day.
PoC Code published for High-Severity macOS Sandbox Escape Vulnerability
Tracked as CVE-2022-26696 (CVSS score of 7.8). Apple notes that the flaw allowed a sandboxed process to circumvent sandbox restrictions and that improved environment sanitisation resolved the problem. Successful exploitation would require the attacker to be able to execute low-privileged code on the target system. An attacker could use this to escalate privileges and execute arbitrary code in the context of the current user. On Friday the 18th of November 2022 Regula published the details on the code needed to exploit the flaw, as well as a video demo.
This bug was patched in macOS Monterey 12.4 in May.
Meta Fires Dozens of Employees for Hijacking Users’ Facebook and Instagram accounts
Over two dozen employees and contractors over the past year have been allegedly sacked for compromising and taking over user accounts. Including those fired were contractors who worked as security guards at the social media firm’s facilities and were given access to an internal tool known as “Oops” which stands for “Online Operations”. This tool is reported to have processed around 50,270 reports in 2020. One case involved a contractor who was fired after an internal investigation found that she reset multiple user accounts on behalf of hackers in return for receiving bitcoin payments for her services.
Cisco Secure Email Gateway Filters Bypassed Due to Malware scanner issue
An anonymous researcher has discovered several methods that can be used to bypass some of the filters in Cisco’s Secure Email Gateway appliance and deliver malware using specially crafted emails.
The researcher is quoted as saying “As the attack complexity is low and exploits have already been published by a third party there must be no further delay in making the threads publicly known”. These methods rely on error tolerance and different MIME decoding capabilities of email clients. These methods work against Outlook, Thunderbird, Mutt, Vivaldi and other email clients.
Cisco has responded with a bug report, claiming that the issue affects its ESA product when running default configurations.
More information can be found in the below links:
Full Disclosure: Cisco Secure Email Gateways can easily be circumvented (seclists.org)
GitHub - noxxi/mime-is-broken: Test cases for broken MIME and tools to generate and process these
Ransomware incidents now make up the majority of the British government’s crisis management “Cobra” meetings
Ransomware incidents in the United Kingdom are now so impactful that the majority of the British government’s recent cobra crisis management meetings have been convened in response to them rather than other emergencies.
France’s Data protection authority CNIL recommending burner phones to world cup fans for Qatar apps
France’s data protection authority CNIL is recommending fans travelling to the World Cup should “Ideally travel with a blank smartphone or an old phone that has been reset. They claim, “Special care should be taken with photos, videos, or digital works that could place you in difficulty concerning the legislation of the country visited”.
Foreigners visiting the country are required to download two applications, the official World Cup app “Hayya” and the Covid-tracking app “Ehteraz”. Experts have classified the apps as a form of spyware because they would provide the Qatari authorities with wide access to people’s data as well as the power to read, delete or change content and even make direct calls.
References:

81% Increase in Large-Volume DDoS Attacks

LockBit ransomware is now moving to a triple extortion tactic

Fake POCs on GitHub Target Security Researchers